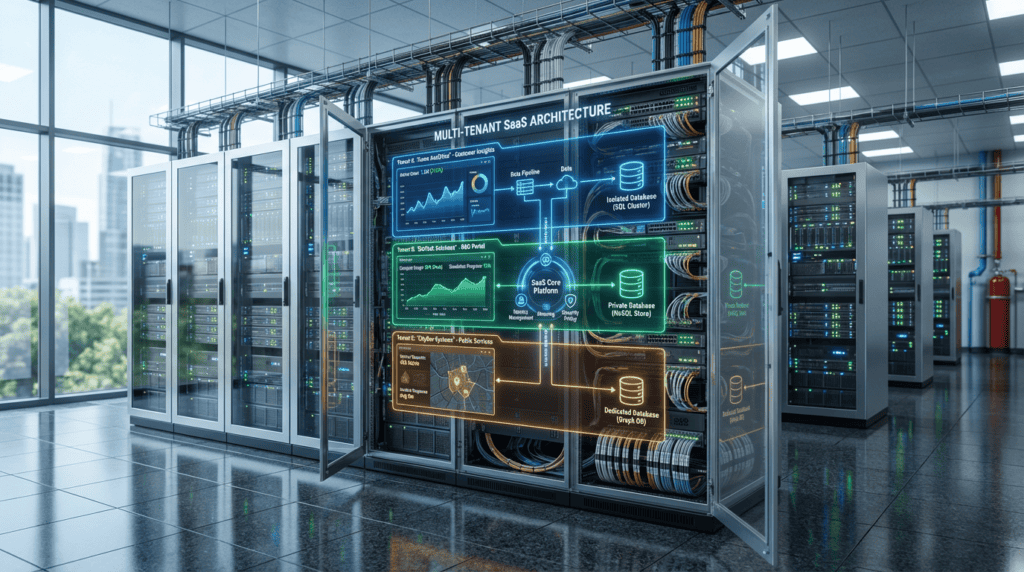
Building a scalable software business requires a delicate balance between operational efficiency and rock-solid data privacy. Modern industry leaders like Salesforce and Shopify achieve this through multi-tenant SaaS architecture, a model where a single software instance serves thousands of customers simultaneously. By sharing core infrastructure while maintaining strict logical isolation, companies can drastically reduce overhead and accelerate deployment cycles. This architectural approach ensures that every customer enjoys a premium experience without the astronomical costs of dedicated hardware.
Think of this structure like a modern luxury condominium where every resident has their own private key and customized interior, yet everyone shares the same foundation, plumbing, and security. In a digital environment, this means your code and compute power are pooled for maximum performance, while unique tenant IDs act as invisible walls to keep sensitive data protected. Mastering these data isolation frameworks is the key to building a platform that scales effortlessly from ten users to ten million. Success lies in creating a system that feels exclusive to every tenant while remaining unified at its core.
Key Takeaways
- Multi-tenant SaaS architecture is the essential foundation for scaling software businesses, allowing a single instance to serve millions of users while drastically reducing operational overhead and infrastructure costs.
- Robust data isolation must be enforced at the infrastructure level through unique tenant IDs and granular role-based access control to prevent data leakage and the ‘noisy neighbor’ effect.
- Architects must choose between siloed database models for high-compliance security and pooled models for maximum cost efficiency, or leverage a hybrid approach to serve both small and enterprise clients.
- Unified operations and automated workflows for onboarding and billing transform infrastructure into a competitive advantage by enabling simultaneous global deployments and feature updates across the entire tenant base.
Core Components of Tenant Isolation Frameworks
Building a robust multi-tenant framework begins with a sophisticated tenant identification and request routing layer. This mechanism ensures that every incoming packet or API call is instantly associated with a specific client ID as it enters the system. Once identified, the routing engine directs these requests to the appropriate logical environment while maintaining strict boundaries between different customer datasets. By embedding this identification process at the infrastructure level, developers can prevent data leakage and ensure that one tenant’s heavy usage does not degrade the experience for others. This foundational layer is what allows a single software instance to behave like a dedicated private environment for thousands of unique users.
The security of this shared environment is further reinforced through a granular role-based access control (RBAC) system tailored for multi-tenancy. Within this framework, permissions are not just defined by user roles, but are also scoped strictly to the tenant’s specific organizational boundaries. This dual layer of authorization ensures that an administrator for one company cannot accidentally or intentionally access the resources of another client. Modern SaaS architectures often integrate these identity providers with automated provisioning workflows to streamline how new users are onboarded into their respective silos. Implementing such rigorous access controls is essential for maintaining the high level of trust required for enterprise-grade software solutions.
Beyond simple access, these core components must be designed to handle the dynamic scaling needs of a growing SaaS business. A well-architected isolation framework allows for the seamless addition of new tenants without requiring manual reconfigurations of the underlying database or server logic. Orchestration tools work in tandem with the routing layer to balance loads and manage resource quotas according to specific service level agreements. By prioritizing these technical mechanisms during the initial design phase, agencies can build platforms that are both cost-effective and inherently secure. This strategic approach to infrastructure positions a product to scale globally while protecting the integrity of every customer’s data.
Evaluating Silo vs Pool Database Strategies
Choosing between a silo or pool database strategy is one of the most consequential decisions a SaaS architect will make during the initial design phase. Under the silo model, each tenant is granted a dedicated database instance, creating a physical barrier that ensures maximum data isolation and security. This approach is particularly attractive for high compliance industries such as healthcare or finance where regulatory requirements often mandate strict data residency. While this setup simplifies custom configurations and backup management for individual clients, it often leads to higher operational overhead and increased infrastructure costs. Scaling a siloed architecture requires sophisticated automation to manage hundreds of disparate database instances simultaneously without draining engineering resources.
The pool model takes the opposite approach by housing multiple tenants within a shared schema, using unique tenant identifiers to logically partition data. This strategy is the gold standard for maximizing cost efficiency because it allows for the highest possible density of users per unit of compute power. By centralizing resources, development teams can push updates and manage migrations across the entire customer base with significantly less friction. However, this efficiency comes with the challenge of the noisy neighbor effect, where one tenant’s heavy usage can negatively impact the performance of others. Architects must implement robust throttling and resource monitoring to ensure that the shared environment remains stable and performant for every user.
Strategic partners must evaluate these models based on long term business goals rather than immediate technical convenience. Many modern SaaS platforms eventually adopt a hybrid approach, placing smaller customers in a shared pool while offering dedicated silos as a premium tier for enterprise clients. This tiered infrastructure allows a startup to remain lean during early growth while maintaining the flexibility to land large, security conscious contracts later on. Ultimately, the decision hinges on balancing the immediate need for resource optimization against the future requirement for granular data control. Selecting the right path early prevents costly migrations and ensures the platform can scale alongside its most demanding customers.
Infrastructure Management and Unified SaaS Operations
Transitioning to a unified multi-tenant architecture requires a strategic shift from managing individual silos to overseeing a cohesive, collective infrastructure. This approach centralizes critical operations such as tenant onboarding and automated billing, ensuring that every new customer experiences a frictionless entry into the platform. By automating these foundational workflows, engineering teams can eliminate the manual bottlenecks that often plague scaling startups and enterprise providers alike. A unified operational layer allows for global deployments that remain consistent across the entire tenant base, regardless of geographic location. This level of control is essential for maintaining high performance while reducing the overhead associated with bespoke configurations.
Effective infrastructure management also hinges on the ability to handle a tiered tenant base through sophisticated resource allocation. High-value enterprise clients may require dedicated performance guarantees, while smaller accounts thrive on the efficiency of shared compute and storage. Modern SaaS operations utilize intelligent routing and tenant identification to enforce these service level agreements dynamically. This ensures that resource-intensive tasks from one customer do not degrade the experience for others sharing the same underlying hardware. By implementing robust monitoring and logical isolation, developers can maintain a secure environment that scales horizontally with ease.
The ultimate goal of unified SaaS operations is to transform infrastructure into a competitive advantage rather than a maintenance burden. Centralizing the codebase and database schema updates means that security patches and feature releases roll out to every tenant simultaneously, drastically shortening the development lifecycle. This streamlined delivery model enables agencies to build platforms that are both resilient and highly adaptable to market changes. As the system grows, the synergy between automated infrastructure and multi-tenant logic provides the stability needed for long-term success. Investing in this high-level architectural framework positions a software product to lead in a crowded and demanding market.
Balancing Efficiency and Isolation in Multi-Tenancy
Selecting the right multi-tenancy model is a foundational decision that dictates the long-term trajectory of your SaaS platform. While shared infrastructure offers unparalleled cost efficiency and streamlined maintenance, the increased operational complexity requires a robust strategy for data isolation and resource management. Engineering teams must weigh the benefits of high-density resource sharing against the specific security and performance requirements of their target market. A well-executed architecture ensures that as your tenant base grows, the system remains resilient and responsive without requiring a linear increase in overhead. This strategic balance allows your agency to deliver a product that is both economically viable and technically superior.
Scalability depends on a framework that can adapt to diverse customer needs without fracturing the core codebase. By implementing sophisticated tenant identification and logical partitioning, developers can offer the customization users expect while maintaining a single, manageable instance of the application. This approach positions your firm as a strategic partner capable of building enterprise-grade solutions that handle complex workloads with ease. Future-proofing your SaaS infrastructure involves anticipating the friction points of growth and addressing them through architectural rigor. Ultimately, the architecture you choose today becomes the engine that drives your platform’s ability to dominate its market segment tomorrow.
Frequently Asked Questions
1. What is the primary benefit of choosing a multi-tenant architecture?
The main advantage is the drastic reduction in operational overhead and infrastructure costs. By sharing core resources while maintaining logical isolation, you can scale your platform to millions of users without the expense of dedicated hardware for every client.
2. How do you ensure one customer cannot see another customer’s data?
Data privacy is maintained through unique tenant IDs that act as invisible boundaries within the system. These identifiers are embedded at the infrastructure level to ensure that every API call and database query is restricted to a specific client’s logical environment.
3. Will a heavy user on the platform slow down the experience for my other clients?
A sophisticated routing and identification layer prevents any single tenant from degrading the performance of others. By managing resources at the infrastructure level, you can ensure that compute power is distributed fairly and that high usage remains isolated.
4. How does multi-tenancy compare to a traditional single-tenant setup?
While a single-tenant setup requires separate instances for every customer, multi-tenancy uses one unified instance to serve everyone. This approach allows you to deploy updates instantly to your entire user base while significantly lowering the cost of maintenance.
5. Is it possible to customize the experience for individual tenants in a shared environment?
Yes, you can provide a highly customized experience by allowing tenants to modify their own private logical settings. Much like a luxury condo, the foundational infrastructure is shared, but the interior configuration and user interface can be tailored to meet specific business needs.
6. How is a request routed to the correct tenant within the system?
Every incoming packet is instantly associated with a specific client ID by a sophisticated request routing engine as it enters the system. This mechanism directs the traffic to the correct logical environment, ensuring that data remains secure and isolated during processing.